Ransomware As A Service (RaaS) Explained
What is Ransomware?
Ransomware, which dates back to 1989, is a form of malware that infects and takes control of a computer user’s machine, or secure documents stored on it, to extort money.
Ransomware is a malware format that encrypts the files of a victim. The attacker then demands that the victim be liable for payment to restore data access. Instructions for paying the money to acquire the decryption key are shown to users. Ransomware as a service (RaaS) is a ransomware infrastructure rented out on the dark web to hackers. This is a simple platform to access ransomware attacks and install them on the victim’s machine to acquire the extortion amount.
How do RaaS attacks work?
The majority of ransomware victims fall victim to Social Engineering Attacks. The term ‘social engineering’ refers to a wide variety of malicious activities carried out through human interactions. It uses psychological manipulation to lead users to make security errors or to provide sensitive information. Many individuals and organizations fall prey to these types of attacks.
The real-world consequences of a successful cyberattack were highlighted this month when ransomware shut down one of the United State’s biggest pipelines.
Colonial Pipeline said that after being the victim of a cyberattack, the company was forced to shut down operations and freeze IT systems proactively. The FBI blamed the attack on DarkSide, a cybercriminal gang believed to be based in Eastern Europe, and Colonial reportedly paid a $5 million ransom to the group.
The increased number of cyberattacks and data breaches have roesulted in substantial monetary and non-monetary losses to businesses across industries which is why UnitedLayer® offers automated, robust cybersecurity, compliance, and risk management programs based on the most comprehensive set of frameworks, benchmarks, and guidelines available, boosting confidence in the company’s security compliance posture.
What steps should businesses take for ransomware protection?
- Educate your employees: Employees can serve as the first line of defense against online threats, actively helping prevent malware infiltration into the organization’s system. Employee education about warning signals, safe practices, and responses, along with a robust security program, can go a long way toward preventing these attacks.
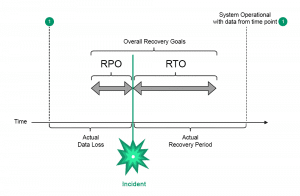
- Employ a data backup and recovery plan for all critical information: Backups are essential for minimizing the effects of malware threats. To access the data in the event of a ransomware attack, store it on a separate device or offline.
- Perform a Risk Assessment: A Risk Assessment is a premium and practical way to help protect your organization. Risk assessments help you identify and resolve vulnerabilities in your IT security and privacy. Following a plan based on a risk assessment will significantly reduce your risks, saving you time and money in the long run.
How UnitedLayer® can help
UnitedLayer® offers a variety of security solutions that not only resolve the security concerns outlined in this blog but can also be customized to suit your organization’s specific security needs. Let’s take a look at UnitedLayer’s® portfolio of products and see how they address the security concerns, as well as how they can work together to protect your business better.
-
- Compliance Automation: We provide regular assessments of security vulnerabilities with prescriptive remediations across your entire hybrid infrastructure (cloud, on-premises, and containers). Regular reports/documentation to support compliance with internal security policies to expedite the auditing process. We have the richest library of security frameworks (NIST, DISA, etc.), benchmarks (CIS OS, cloud, and Docker), and compliances (SOC, ISO, GDPR, PCI, HIPAA) with advanced compliance mapping. Co-author of both Docker and Kubernetes Security Benchmarks from the beginning.
- Network Security: Our cutting-edge security solutions protect client infrastructure from any external security threats. We provide IPsec VPN, SSL VPN, IDS/IPS services for secured access to cloud infrastructure. In addition to this, we also offer DoS/DDoS protection against all types of network attacks and threats. We have multiple firewalls in place for each customer deployment to increase network security redundancy.
- Application Security: Our application security services ensure the safety and security of your sensitive business information from any security threats. With application penetration tests or ethical hacking, we help organizations identify the security vulnerabilities present in the application. Our secure code analysis enables organizations to verify that proper security controls are present in the application.
- Virtual Security: We provide security partners like Gateway Firewall, Web Firewall, Application Firewall, DDOS mitigation, VLAN Segmentation, Security Incident Monitoring, Private Cloud implementation with ACL, and lockdown of the ports and IP address along with the encryption of data at rest and in transit.
- Data Security: We use several methods to ensure the integrity and confidentiality of the data we receive from our customers. Our production data is regularly encrypted and backed up. AES-256 is used to encrypt data at rest, while TLS 1.2 is used to encrypt data in transit.
At UnitedLayer®, we have a growing list of managed services, which helps corporations restructure their infrastructure and enhance their responsiveness, optimization, resource efficiency, and flexibility, leading to better and enhanced customer experience and quicker time to market.
Visit our website and register for a free demo today to get a glimpse into what else we have to offer.